The Role of CNP Fraud Prevention in Dark Web Database Breaches
Friendly fraud, policy fraud, and account takeover attacks are becoming more and more prevalent in recent years, and merchants are rightly worried. But the increase in “alternative” fraud methods shouldn’t distract merchants from what is likely to remain eCommerce’s main threat for many years to come: credit card breaches and its consequences, card-not-present (CNP) fraud.
Most transactions around the world are made using credit cards, with the exception of China. There are currently 2.8 billion such cards in circulation worldwide, with around 70% of global households owning at least one. Beyond their widespread availability, they’re also inexpensive to buy on the Dark Web, going for $14-$30 per card on average, though nationality and account balance can drive the price up. No wonder it’s such an easy and reliable method for fraudsters.
Did you ever wonder how bad actors get those credit card details, though? Sure, phishing is a method commonly utilized, especially for vulnerable population segments like the elderly, but the bulk actually comes from database breaches performed by hackers who later sell their loot on the dark web.
Ecommerce data breaches account for 80% of cards-as-payment-related investigations, and the average cost of a data breach in 2021 was almost $4 million annually per company (across all industry sectors).
Choosing the right card for the fraud
As everyone who utilizes their credit card rewards knows, they aren’t all created equal. There’s more to CNP fraud than ‘just’ buying card details off the Dark Web. There are websites and forums where fraudsters can perform market research, report on which cards and issuers work best for which type of fraud, and keep up to date with the latest developments in the credit card fraud sphere.
The journey of a BIN
Due to the nature of the entities being breached, the mass credit card hauls obtained in these hacks often have shared characteristics, such as bank identification number (BIN) or geographical commonalities. Cards from the same issuers are then used across industries and merchants by unrelated fraudsters. As you can see in the graphs below, across Riskified’s merchant network we saw fraud attempts using the same BINs flaring up at different times and industry segments throughout 2020, with no specific pattern. These breaches eventually impact multiple players across the global eCommerce industry – once a card’s details are out there, it will be used by numerous types of fraudsters for many forms of CNP fraud.
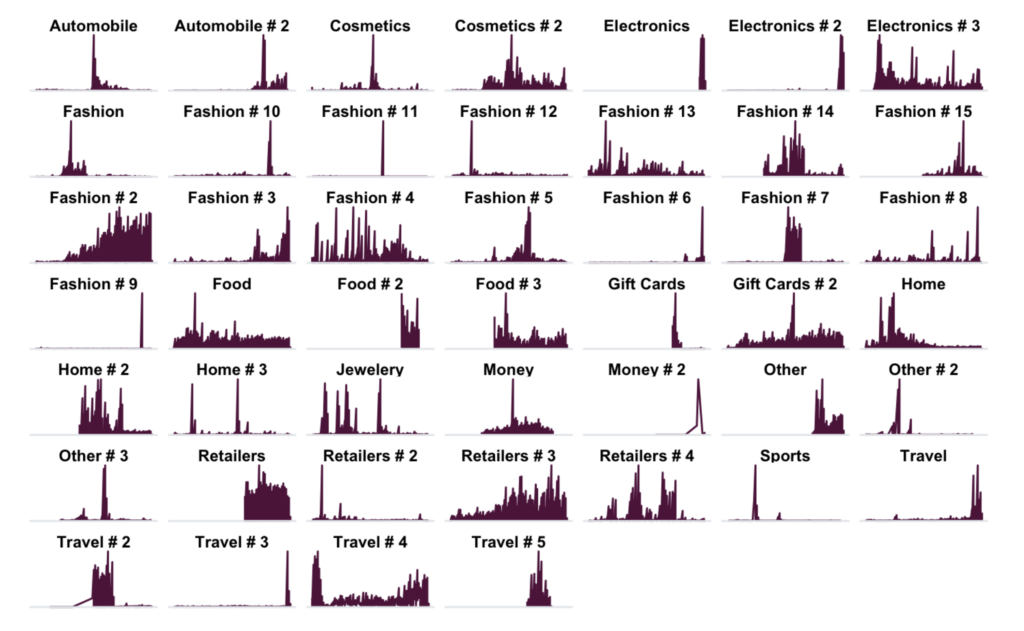
To better understand the problem, let’s zoom in on the journey of one specific BIN, issued by a Canadian bank, across Riskified’s network in 2019-2021:
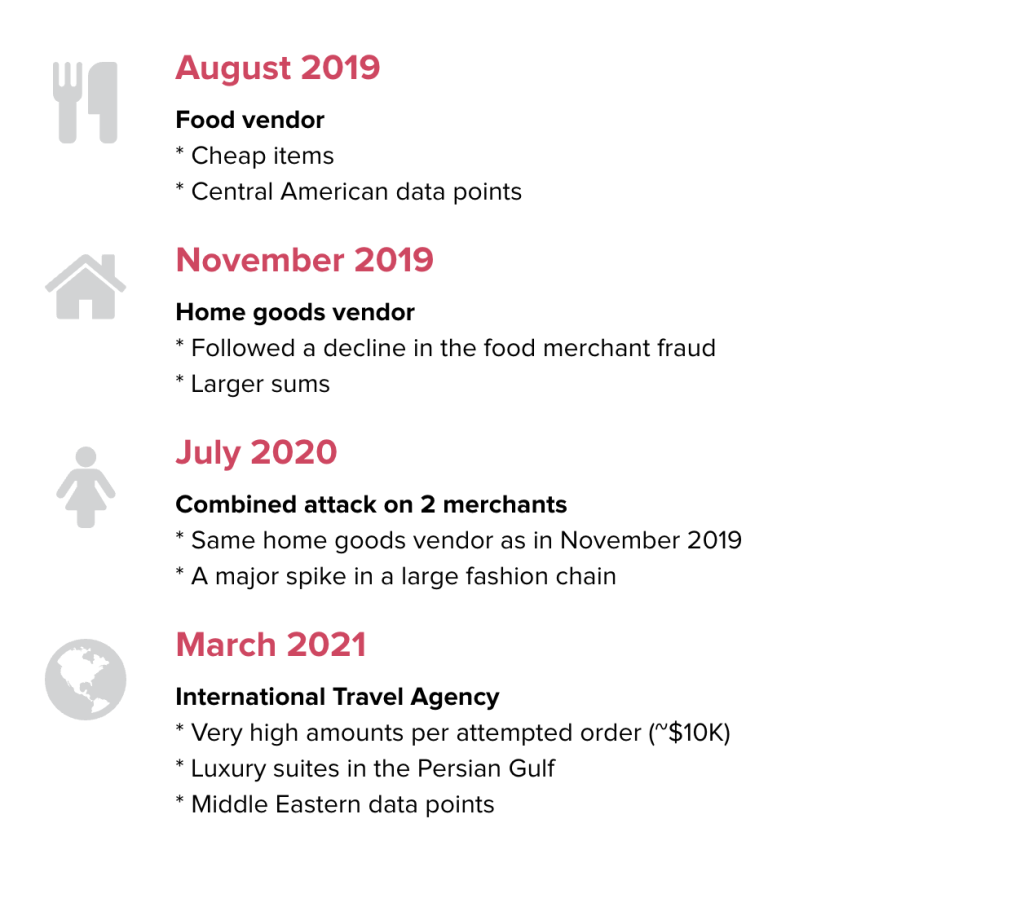
As you can see, we blocked fraud attempts across four different merchants during this period, and each event displayed different fraud characteristics despite using the same BIN.
The bottom line
Riskified has a vast merchant network spanning multiple industries and geographies. This allows us to identify emerging fraud trends across disparate industries, geographies, and specific merchants, and protect against such attacks. Our machine learning models are dynamic, allowing us to recognize the changing risk level of the different BINs and issuers in real-time and automatically factor that into our decision process. This enables us to protect yet untargeted merchants as well – and also recognize when a once-risky BIN has become safer once again, and adjust automatically to avoid consumer friction.
This blog was co-authored by Nimrod Dvir, an analyst on Riskified’s Fraud Intelligence team specializing in fraud rings.