The Dark Side of Delicious: Decoding Food Delivery Fraud on the Dark Web
Food delivery fraud is on the rise. In this blog post, we look to the dark web to learn why, and discover the most popular MOs fraudsters use to score a free meal
In more ways than one, scamming a food delivery service is gateway fraud. Remember when ordering pizzas to the address of an unsuspecting victim was a staple of youthful mischief? Some of the popular food delivery fraud MOs our analysts encounter these days are not far removed from childhood pizza pranks. But what some forms of food fraud lack in sophistication, they offset in the mounting losses they cause.
From the simple practice of ordering a meal, “disposing of the evidence,” and calling to claim a refund because your food never arrived, to more complex account takeover (ATO) scams orchestrated by seasoned fraudsters, food delivery often comes with a side of fraud. A lot of what we know about food delivery fraud we discover on the dark web, where fraudsters brag about their spoils and share tips on how to hustle a hot meal. In this blog post, I’ll explore why the sector is attracting so much fraudulent activity and how it is affected by the rising ATO trend. I’ll also share the most popular MOs Riskified analysts identified on the dark web.
Fraudsters enjoy the hospitality
Recent years saw the bulk of food delivery activity move online, from restaurant chains going digital, to the boom of delivery services such as GrubHub, Uber Eats, DoorDash, and Deliveroo.
The customer-first culture of the business, together with the need to fulfill orders quickly, means that transactions are less likely to be questioned, and complaints are often resolved with swift action in favor of the customer. Additionally, fraud prevention is deprioritized because average order values are relatively low. Due to high volume, relatively low-values, and easy accessibility, online food is tempting serial fraudsters and random opportunists alike.
This gave rise to one of the most common fraud MOs in the food delivery sector: carding. We’ve learned that fraudsters visit food delivery websites to test out credit card details they bought on the dark web—manually or using bots—before trying them out on more high-stakes goods. In this practice, scoring a meal is simply a bonus on the way to more lucrative fraud.
These days especially, the dark web is teeming with activity around food delivery fraud. COVID-19 introduced an unprecedented dependency on these services. In a recent article, Foodnavigator called the industry the pandemic’s biggest winner. While growth amid economic uncertainty is encouraging, a sharp rise in demand can overwhelm and debilitate fraud management systems. Plus, many existing fraud prevention methods are based on a system of rules reflecting familiar customers and shopping behaviors. A mass of never-before-seen customers and a sharp rise in volume can completely throw off the more rigid fraud prevention methods, making merchants more vulnerable.
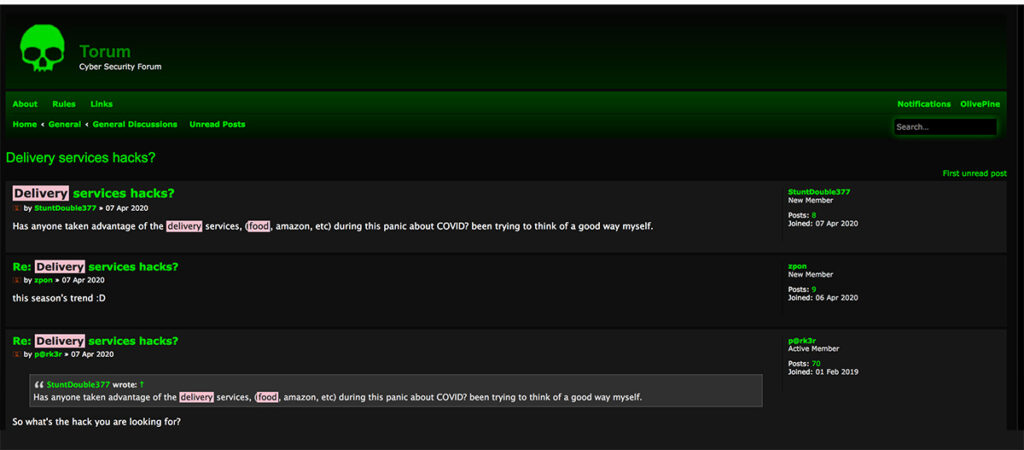
Welcome to the Dark Web’s school of fraud
More than fraud tips and tricks, the dark web is the ultimate source on who fraudsters are targeting. Right now, fraudsters are setting their sights on many players in the online food sector, from delivery apps (Doordash and Uber Eats come up often in chats) to food subscription services and restaurants managing their digital ordering in-house (Dominos is a favorite). Many restaurateurs and other food merchants are offering digital gift cards to grow revenue and cater to their remote clientele. These high-risk goods are also on fraudsters’ radars.
Fraudsters targeting delivery apps often cover their tracks by erasing their cookie histories and using voice-over-IP (VOIP) manipulation as they test out stolen CCs. Delivery policy abuse, also classified as liar buyer fraud, is a hot topic too. A common tactic is the “leave at side door” scam. One fraudster doling out tips on a dark web forum encouraged a fraud-curious user to try this entry level social engineering technique before attempting credit card fraud. Adding a ‘leave at side door’ note at checkout, he said, makes the fraudulent claim more plausible, and the reimbursement as good as guaranteed.
One enterprising fraudster found a creative way to make a quick buck on the dark web. They are offering their eBook, How to Get Free Food from Uber Eats, Just Eat, and Deliveroo, for just $4.99.
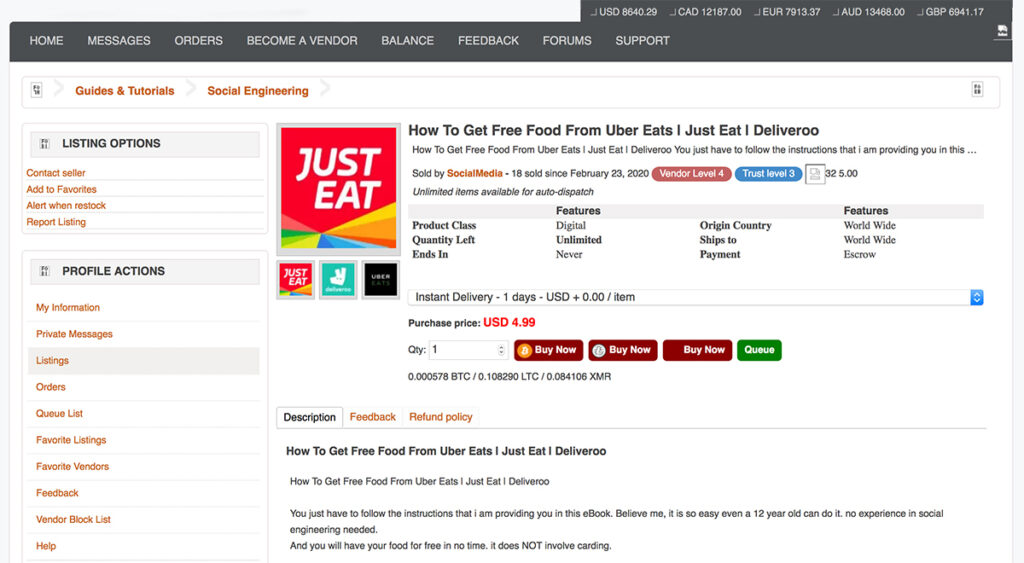
Ambitious newcomers attempting account takeover (ATO) fraud can easily get advice from experienced fraudsters. The threads we’ve seen offer the following tips for ordering via another person’s account:
- Change the phone number associated with the account immediately
- Turn off all account notifications
- Opt for pickup whenever possible
- Use app credentials, but favor PC for placing the order
- If you use your phone, better to use a burner with the GPS and location settings off
Account takeovers: online food’s toughest challenge
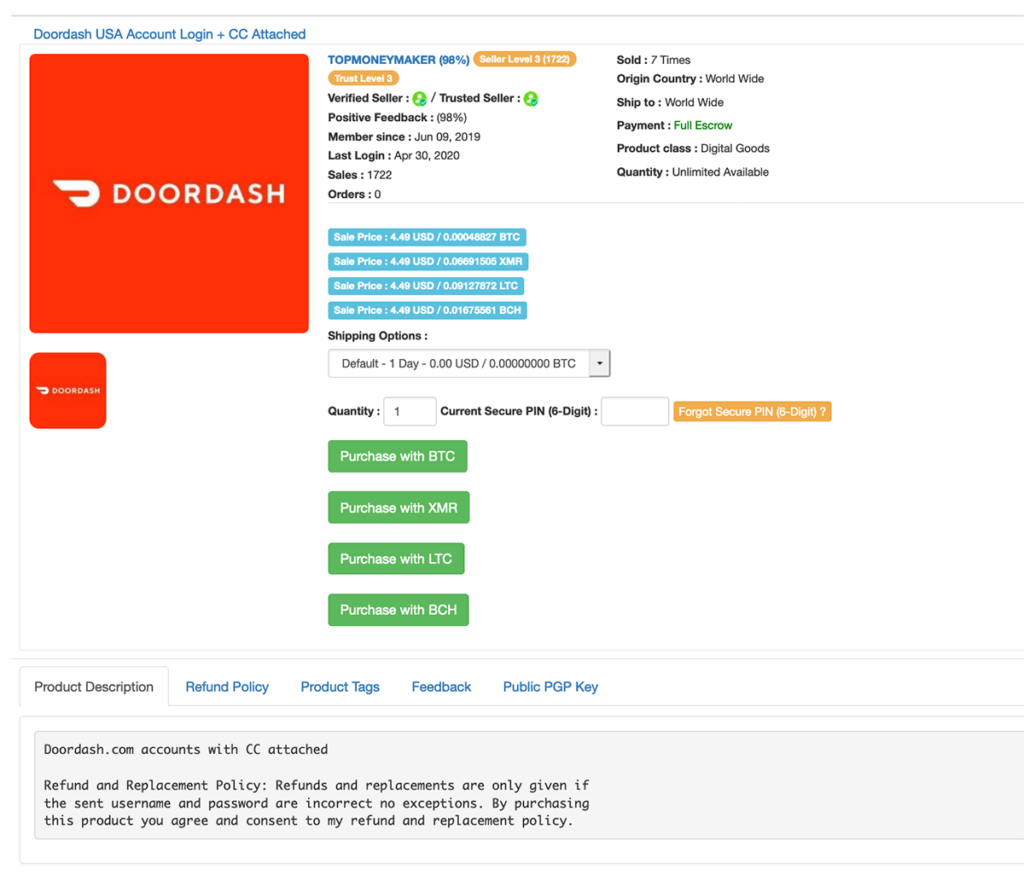
ATOs are having a moment, and food delivery websites are feeling the heat. Many restaurant chains and online delivery hubs have been the target of data breaches in recent years, leading to millions of account credentials being sold on the dark web. London based Deliveroo, DoorDash, and Google-backed Indian delivery app Dunzo all suffered a breach within the past year. Among the bargains our analysts found on the dark web are DoorDash accounts with attached credit cards for $4.49 and Dominos accounts with loyalty points for $1.99.
As more and more of the food and restaurant industry transitions online, accounts will continue to be central, generating both opportunity and added risk. A recent Riskified survey of nearly 4,500 consumers and merchants showed that accounts are instrumental in attracting repeat customers and bigger transactions. At the same time, when accounts are compromised, brands face a difficult loss of both brand reputation and revenue. These days, fraudsters are reacting to the general turmoil by upping their efforts to steal customers’ data. They know that entering a legitimate user’s account increases their chances of success.
Most common fraud prevention methods are not equipped to detect ATO attacks because the approve/deny decision must happen at the login, when minimal information is available. Successful ATO solutions make use of vast networks of customer information and advanced linking capabilities.
What can merchants do?
Fraudster communication on the dark web suggests that since the beginning of the year, fraud prevention methods in the food delivery sector have become more efficient, if still somewhat basic. Common methods include matching card details with CVV codes, address match verification (AVS), and phone verification when an order is placed.
These are all good practices, but experienced fraudsters know how to work around them. To address a growing problem, merchants must understand the MOs fraudsters use and adopt fraud prevention strategies that address them. Fraud prevention technologies that rely on machine learning models for real-time decisions are an excellent match for an industry that prides itself on fast delivery. Using the power of strong customer networks and data linking can help merchants accurately discern the bad actors from the good and adapt to changing order patterns even when sales skyrocket.